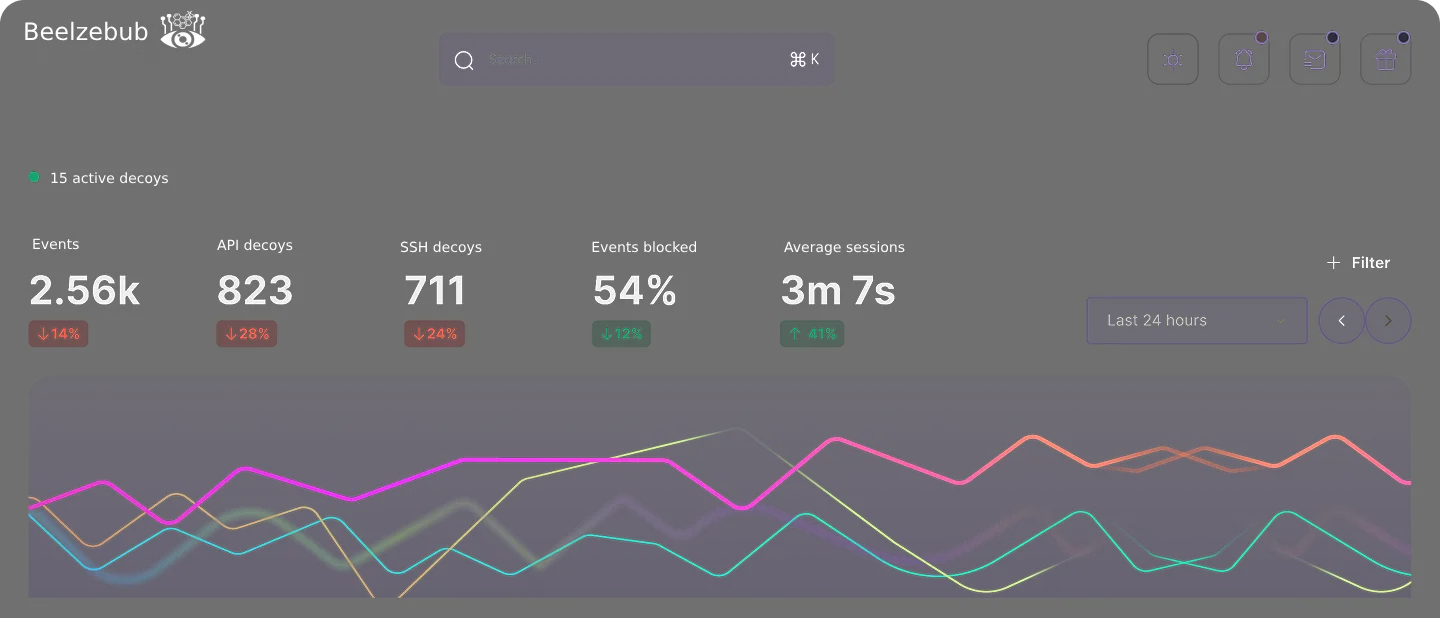
Deceive, Detect, Respond
Deceive
Full-Stack Deception Across Your Entire Infrastructure
Deploy AI-powered decoys everywhere attackers can move—IoT devices, Kubernetes clusters, cloud-native environments, APIs, and even honeypot tools for AI agents. Our open-source framework (1.4K GitHub stars, 450+ weekly installs, 45+ countries) deploys in 1-2 minutes with zero supervision required. When zero-day exploits and supply chain attacks bypass your perimeter, only deception technology catches lateral movement. Trusted by Fortune 500 companies across telecommunications, finance, and critical infrastructure.
Detect
Zero False Positives, 100% Real Threats
Our AI decoys behave like real systems without human supervision, triggering alerts only when attackers interact with them. Centralized dashboard provides complete visibility across your infrastructure while automated threat intelligence analyzes every attack in real-time. No more alert fatigue—every notification is a confirmed breach attempt. Two documented real-world attacks already stopped using our technology.
Response
Autonomous SOC Response in Seconds, Not Hours
AI-powered SOC team performs comprehensive threat analysis—from malware sandbox execution to network traffic analysis—producing clear, executive-ready reports for strategic decision-making. Automated isolation contains threats instantly while our AI agents deliver complete post-mortems. Slash MTTR from hours to seconds and reduce SOC operational costs by 60% with fully autonomous response.
How Beelzebub Works
1) Deploy Full-Stack Decoys
Deploy AI-powered honeypots across your entire infrastructure: Containers, Kubernetes clusters, APIs, AI agent honeypot tools, cloud-native environments and IoT devices in 1-2 minutes. Our open-source honeypot framework creates realistic systems that appear vulnerable while remaining completely secure. Zero supervision required, zero false positives—only real threats trigger alerts.
2) Engage & Analyze Threats
When attackers hit your decoys during lateral movement, our AI honeypots keep them engaged for hours while our autonomous SOC team performs comprehensive threat analysis—from malware sandbox execution to network traffic analysis. Turn attacker persistence into your intelligence advantage.
3) Autonomous Response & Intelligence
Our AI-powered SOC team automatically isolates compromised servers in seconds, stopping lateral movement while generating executive-ready post-mortem reports with actionable remediation recommendations. AI SOC that responds in seconds, reducing operational costs by 60%.
Enterprise Compliance & Regulatory Alignment
Our platform addresses lateral movement detection requirements mandated by NIS2 Directive and DORA regulations, turning your infrastructure into an intelligent defense system for advanced persistent threats. Trusted by Fortune 500 companies across telecommunications, finance, and critical infrastructure.

Here's What People Are Saying
Securing Kubernetes Using Honeypots to Detect and Prevent Lateral Movement Attacks
Compliance Auditor
The initial hype about AI may cool down, but the use of AI is only really gaining in importance, especially in the case of honeypots!
Senior Expert Security, Telekom Security
Beelzebub is an open-source honeypot framework engineered to create a secure environment for detecting and analyzing cyber threats.
Cybersecurity news and industry insight
Beelzebub: Open-source honeypot framework
CISO
Beelzebub: Open-source Honeypot! AI-powered honeypot framework creates a secure, high-interaction environment to detect and analyze cyber threats. It’s designed for low-code deployment and supports multi-protocol decoys like SSH, HTTP, TCP, and MCP to detect prompt injection attacks against LLM agents. Unlike traditional honeypots, Beelzebub uses an LLM sandbox to interact with attackers safely.
Executive Director - EC-Council
The framework generates high-fidelity threat intelligence, detecting command patterns and techniques used by real attackers. The combination of realism and automation allows security teams to operate realistic honeypots without the traditional maintenance and supervision costs. Beelzebub represents a significant evolution in proactive detection: it acts as an early warning system, reduces false positives, and helps refine defenses through real operational information on attacks targeting environments with artificial intelligence.
Senior Manager, Cybersecurity at KPMG
The Beelzebub framework is an advanced honeypot that provides a very secure environment for detecting and analyzing attacks. The framework is very easy to set up and uses artificial intelligence to simulate the behavior of a honeypot.
Security Audit Team Leader - Tejarat Bank
Prompt injection is still an open threat. Beelzebub’s new MCP honeypot catches it in action,right inside your agent pipeline. Trigger logs. Attack metrics. Safer models.
Integrate seamlessly


































Frequently Asked Questions
Beelzebub uses Large Language Models (LLM) to create high-interaction honeypots without the complexity and security risks of traditional solutions. Our AI acts as realistic Linux server, API services, MCP Tool, all service based on TCP. Engaging attackers for hours while remaining completely secure.
Key differentiators:
- Zero false positives - only real threats trigger alerts
- No human supervision required - fully automated operation
- High interaction without risk - LLM provides safe, realistic responses
- Multiple honeypot with single instance - With a single instance of Beelzebub, you can configure thousands of honeypots with different behaviors.